Enterprise applications are deployed in a complex and fragmented environment that consists of networks, operating systems, and databases that are all interconnected. Fragmentation and a lack of a clear and foolproof security roadmap are common results of this practice.
When it comes to app security, developers prefer to rely on outdated and ineffective methods that frequently fail in the face of today’s sophisticated threats. App security is no longer a reactive response to attacks thanks to the emergence of rasp security solutions, which have the ability to handle several layers of security management at the application, infrastructure, and security levels. Ad-hoc measures used by developers when confronted with risks prompted the development of RASP security, or runtime application self-protection.
Secured by RASP (Real-time Application and Protocol (Runtime Application Self-Protection)
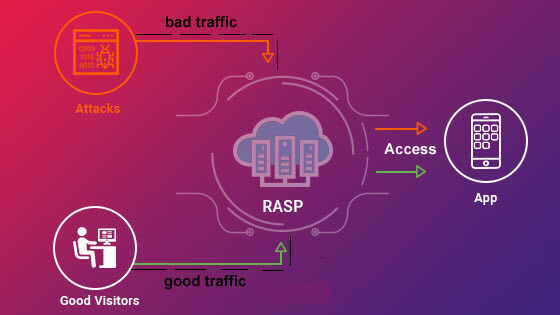
In order to combat runtime assaults on software’s application layer by increasing visibility into hidden vulnerabilities, RASP, an innovation in the application security ecosystem, has been developed. Integrates with a program or its runtime environment and continually intercepts calls to the application so that they may be checked for security vulnerabilities. There is no need to wait for a threat to damage the app before using a RASP security program. An alternative is to actively scan incoming traffic for malware and block bogus calls from being executed inside the app.
What is the Process of RASP Security?
An application’s runtime activates RASP technology, a server-based solution. When RASP is integrated into the app’s source code, or when an external coat is applied to a finished program, it may be activated with a single command. Since the code-base may be changed depending on business needs, most developers prefer utilizing trigger calls inside the code. By using this strategy, you are able to carefully specify the protection settings while simultaneously increasing the runtime by eliminating security checks that are not essential.
The incoming traffic to the server and APIs of the application is monitored by a RASP layer, which sits side by side with the application code. The RASP layer sits between the application and the server, screening all requests without affecting the application’s performance.
As a WAF, RASP can identify attack vectors, but it can also conduct countermeasures in the event that a threat is permitted to take hold. A user session might be terminated or traffic analysis and vulnerability monitoring could be performed during runtime to determine the effect of a vulnerability on the program. RASP has a lower rate of false positives since it is close to the application’s most dangerous code.
RASP Security’s Pros:
In contrast to a firewall, RASP is able to defend the program itself, rather than only protecting the network. RASP is able to deliver a contextualized service because of its ability to take essential information from the codebase, APIs, system configuration, runtime data, logic flow, and so on.
· Penetration Testing using a Smart Approach
Penetration testing may be made more efficient by using RASP technology. Anomalies may be detected by the program, as previously described, and appropriate responses can be taken. Reprogramming and testing various areas are also made simple.
· Sophisticated Incident Reaction
Improved incident reaction times and intelligence are two key benefits of RASP technology. Real-time data is available to developers thanks to the in-depth insight into the application runtime and active security logging mechanisms. As a result, security designers may create more effective systems by using the monitoring capabilities more effectively.
· The Ability To See Inside The Attack At Runtime:
Runtime application security data was previously unavailable, hence the security structure had to be created based on hunches and predictions. With the addition of RASP software, many of these things will be altered. In order to better align the development process with real-time security events, RASP provides significant insight into the application’s run-time events.
· Involvement In The Development Of Compliance
As well as offering security, RASP technology dramatically enhances application development. It’s easy for developers to find the most important attack assets and vulnerabilities thanks to extensive testing and real-time data analysis. Allows for more secure and compliant apps with fewer vulnerabilities every time.
· Anti-Protection for Older Software
A company’s legacy application is a priceless resource. However, contemporary improvements make it difficult to safeguard ancient programs. It’s tough to provide security against new attacks since most legacy programs are built-in antiquated code bases. Using RASP technology, you can wrap your legacy software with sophisticated security features without having to modify your current code.
· Additional Layer of Defense
When used in conjunction with WAF and IPS, RASP provides an additional layer of security to help keep your network safe and secure. In contrast to the firewall, RASP technology actively monitors the app’s runtime for dangers, eliminating them as they occur.
· Self-Protection
An autonomous security system, RASP can identify and remove threats without the need for human interaction once it is installed. As a result, a self-protecting application is necessary.
The program defends itself during runtime and provides you with detailed security events and runtime statistics as a result of this protection.
· Cost-Effective
Because of the high level of protection it provides, RASP is a very cost-effective option. Your applications will be protected from attacks and actively provided by this low-maintenance technology
Security-related event logs. In other words, you get all of the above in one package: greater security, better analytics, and better development.
· Higher-Quality Developer Education
Because it decreases application development’s inherent risks, security teams must include developer training as a core component of their efforts. You may supply more accurate information about the application’s vulnerabilities and attack-prone locations by actively using RASP data. Therefore, making it easier to design applications that are more secure.
Conclusion
With the help of WAF and testing, a RASP security solution is the game-changer your company needs to cope with today’s complex threat environment. Appsealing‘s RASP monitoring, traffic analysis, and learning capabilities make it possible to add a RASP layer to applications, giving them the ability to detect and repel assaults with extreme precision. RASP is a must-have security solution because of its frictionless, no-code deployment and integration, which has no influence on the app’s overall speed.